Archive
Duplicate cleaner
Duplicate cleaner is a useful program to help you organize the contents of your home hard drive or corporate network.
You’d be surprised just how many redundant or duplicate files you could find forgotten in an obscure documents folder. Duplicate Cleaner will deep scan for all types of files – photos, music, films/video, Word documents, PowerPoint presentations, text files – you name it, if it appears twice on your computer then Duplicate Cleaner will find it. Once these files are found you are provided with helper tools to enable you to select which copies to delete or move.These files can be deleted to the recycle bin, moved into an archive elsewhere, or replaced with hardlinks.
Screenshot
Features
- Find Duplicate Files by content, fast!
- Cleaner hard drives means faster performance
- Fast Scanning and accurate duplicate comparison (Uses the MD5 Hash algorithm)
- Deep scans music – locate duplicate music formats (MP3, iTunes, etc)
- Flexible search parameters
- Intelligent Selection Assistant
- Search home or networked drives
- Search multiple locations
- Export / Import results in CSV format
- View Path,Size and Date of files
- Large, resizable list window
- Image preview window
- Delete duplicate files to the Recycle bin
- Move dupe files to a new location
- Turn duplicate file into hard links (NTFS file systems only)
- Protection for Windows and system files
- Supports multiple languages
- No Spyware, Adware or any other rubbish
- Free!
Free Hide Folder
Why do you need Free Hide Folder?
Most people have many files or folders on their computer which they do not want to others see or use them. If you are interested in protecting your personal information, Free Hide Folder is just what you are searching for. With Free Hide Folder you will protect your files avoiding them to be being modified, seen or erased by other users.
Platform: Windows 9x/Me/NT/2000/XP/2003/Vista/7
File Size: 875 KB
License: Freeware
Using Free Hide Folder
It’s actually very easy to hide a folder with Free Hide Folder. It takes only a few mouse clicks. First, you need to run Free Hide Folder, locate and select the folder you want to hide, and then click Hide Folder button to hide folders.
Key Features:
• Hide your folder completely. Unless you unhide it yourself, nobody can find it.
• Password protection when running program.
• No file system structure modifications needed.
• Any number of folders may be hidden at the same time.
• Easy-to-use user interface.
• 100% Spyware FREE. This software does NOT contain any Spyware, Adware or Viruses.
Homepage: http://www.cleanersoft.com/hidefolder/free_hide_folder.htm
Files Terminator Free
Files Terminator Free is an easy to use application that allows users to permanently delete their files and wipe free disk space.
The utility protects the users privacy by permanently delete sensitive documents, images, videos and other files and by overwriting the free disk space.
The software uses several shredding methods (one pass Pseudorandom, British HMG IS5, two pass Russian GOST P50739-95, three pass US DoD 5220.22M, seven pass German VSITR, Canadian RCPM TSSIT OPS-II, Bruce Schneier and the 35-pass Peter Gutmann) and supports drag and drop for easier use.
During file shredding the content of the selected files are overwritten several times with random data and predefined characters and cannot be recovered any more.
Finally, Files Terminator Free is a quick and easy to use application with a user-friendly interface that helps users permanently delete sensitive documents and swap free disk space.
OS: Windows XP (95/98/2000/ME/Vista/7)
License: Freeware
Size: 1,80 Mb
Authors: Marcello Pietrelli & Gianni Baini
Language: English/Italian
Homepage: http://elefantsoftware.weebly.com/files-terminator.html
Download:http://elefantsoftware.weebly.com/uploads/4/5/2/2/4522293/setup_files_terminator_free_1.1.0.0.exe
Start Menu Cleaner
Start Menu Cleaner is a freeware utility, which cleans the start menu by removing unneeded shortcuts and folders. Most applications add folders and shortcuts to the start menu. The problem is, when you remove a program, sometimes its folders and shortcuts remain in the start menu. After a while, this can make the start menu messy and cluttered up. Start Menu Cleaner scans all shortcuts in your start menu and removes empty folders and shortcuts which points to files that no longer exist. The result is a smaller, cleaner and more efficient start menu.
Download Start Menu Cleaner Version 1.51 (clean151.zip, 38KB)
This utility requires MSVBVM50.DLL and OLEAUT32.DLL. Please download them if you do not have them already. After you get the files, extract them to your Windows\System folder.

Homepage: http://www.iceview.com/
Virtual CloneDrive
Virtual CloneDrive
At times, you might need to mount an ISO file to view the contents of the ISO file, or may be, you might want to mount a Windows OS ISO file to quickly copy ISO contents to create a bootable USB flash drive. Though Windows 7 doesn’t support ISO mounting out of the box, there are some good free utilities to mount an ISO file.
In general, one needs to burn the ISO file to CD/DVD to view and use the contents of the ISO file. But if you don’t want to burn the ISO to a CD/DVD, you can use third-party tools such as Virtual CloneDrive to easily mount ISO files.
Virtual CloneDrive is a completely free and easy-to-use ISO image mounting software for Windows XP, Vista, and Windows 7. It can easily mount .CCD, .BIN, .UDF, .ISO, .IMG, and .DVD files.
How to use it:
- Download and install the software from here.
- Right-click on the ISO image file that you want to mount and select Mount (Virtual CloneDrive (drive letter)).
- Now, you can see the new virtual drive in the explorer (My Computer).
Example:
For example, if you want to mount a Windows 7/Windows 8 ISO file to copy installation files, you would perform following steps:
- Navigate to the drive or folder that contains Windows 7 ISO file.
- Right-click on the ISO file, and select Mount (Virtual CloneDrive (drive letter))option. Also notice the drive letter provided in the option.
- Now open Windows Explorer and open the virtual drive to see the ISO file contents. You can now copy all the contents of the drive to your desired drive or folder.
License: Freeware
Requirements: Windows 98, Windows ME, Windows 2000, Windows XP, Windows Vista or Windows 7 (32 or 64 bit)
NetUse
 NET USE command is used to associate a local drive letter or device name with a shared network drive or device. Most often, the NET USE command is used for network drive mapping.
NET USE command is used to associate a local drive letter or device name with a shared network drive or device. Most often, the NET USE command is used for network drive mapping.
The NET USE command can be used also to disconnect a computer from a shared resource, or to display information about computer network connections.
The NET USE command also controls persistent net connections.
What network resource can I connect to using NET USE?
When connecting to a network device using the NET USE command or the NET CONNECT command, you can connect to any of the following:
- printer – LPT1 thru LPT4,
- serial port – COM1 thru COM4,
- AUX1 thru AUX4
- logical drive – A: thru Z:
Logical drives are most commonly referenced devices when using the NET USE command.
Difference between NET USE and NET CONNECT
The commands NET USE and NET CONNECT are interchangeable. Originally IBM introduced the NET USE command and Microsoft used the NET CONNECT command. The NET USE command is being used more often now and is the preferred method these days.
Where NET USE is used?
The NET USE command is only available on client computers, that is most often on desktop workstations. A “client computer” in this context refers to the relationship of the computer not to the physical configuration. A client computer is the one that connects to somewhere, the one that relies on the target resource. The NETWORK.COM or CLIENT.COM modules need to be loaded for this command to work.
Before you can use any network device or drive, it must have been previously shared using the NET SHARE command from the server machine.
How do I display a list of network connections on my computer?
When you use the NET USE command without parameters NET USE retrieves a simple list of network connections. Go to your Start menu, click Run, type cmd and hit enter. Then, type NET USE and you will see a screen similar to the following output:
| Status | Local | Remote | Network |
| ——————————————————————————- | |||
| OK | H: | \\client-0001\C$ | Microsoft Windows Network |
| OK | O: | \\client-0105\shared | Microsoft Windows Network |
| OK | P: | \\192.168.10.128\QRM | Microsoft Windows Network |
| OK | S: | \\1-nas01\teamddm | Microsoft Windows Network |
| Disconnected | X: | \\01-antivirus-s\mcafeedat | Microsoft Windows Network |
| The command completed successfully. | |||
The NET USE is very useful to get a list of connected network devices. If you need information about some particular network resource that you are connected to, you can use the following command:
NET USE [DeviceName]
For example, this would be the output for “NET USE H:” where “H” is your network drive.
| Local name | H: |
| Remote name | \\client-0001\C$ |
| Resource type | Disk |
| Status | OK |
| # Opens | 1 |
| # Connections | 1 |
| The command completed successfully. | |
How do I make network connections persistent (available after reboot)?
When mapping a network drive, you can tell the computer to remember your mapping after you restart the computer. If you want to make all future connections are persistent (auto-reconnect at login), use the following:
NET USE /Persistent:Yes
or
NET USE /P:Yes
If you want to make all future connections non-persistent, use the following:
NET USE /Persistent:No
or
NET USE /P:No
In this case, mapping will be lost when the computer is restarted.
How do I connect a user to his or her HOME directory?
Connecting a user to his or her HOME directory is often used in corporate setting where each user is allocated some space on the network in addition to his or her personal computer. Making this network location available every time the user logs into his or her computer can be accomplished using the NET USE command in a login script. The following is the way it works:
NET USE [devicename | *] [password | *]] [/HOME]
for example:
NET USE H: /Home
The devicename in this case is the HOME server/folder that is defined in Active Directory (ADUC).
In case you need to use the NET USE command to connect to a password protected file share, use the following:
NET USE [driveletter:] \\ComputerName\ShareName[\volume] [password | *]
[/USER:[domainname\]username] [/PERSISTENT:No]
The following are a few examples of this:
NET USE H:\\CorporateFileServer\Users\%Username%
NET USE W: \\CorporateFileServer\GroupShare /Persistent:No
Are you wondering what the /USER is?
How to specify USER in NET USE?
If you deal with enterprise security, you may need to provide user name to the NET USE command. There are two notations for giving it the user name. In the NET USE command /USER can be specified as:
[/USER:[dotted domain name\]username][/USER:[username@dotted domain name]
Both work the same way.
Another example is:
NET USE X: \\client-0001\ernesto /USER:cappello
This command map the disk-drive device name X with “ernesto” folder shared from “client-001” server using “cappello” account.
If you use SAMBA to share a folder from the server, you have to use:
NET USE X: \\SERVERNAME\FOLDER <SAMBA PASSWORD> /USER:<SAMBA ACCOUNT>
therefore
NET USE X: \\client-0001\xarabas_shared ********* /USER:xarabas
How do I disconnect from a share using NET USE?
If you no longer need a connection to the network share, it is a good idea to disconnect from it so that it does not drain system and network resources. You can do so by using the following NET USE command:
NET USE [driveletter:] /DELETE
This should disconnect.
Important note: You cannot disconnect from a shared directory if you use it as your current drive or if an active process is using it. You can find out whether anything is using your drive by typing the NET USE [driveletter]:
Possible problem with NET USE
Mapping to a resource shared on the network using the NET USE command has some peculiarities. You can encounter a problem when trying to connect to a network share right after you map to it (when doing so in a script).
This is because the execution of the NET USE takes some time. When using the NET USE command in a script to map to a network drive, you may want to wait until the mapping has completed before continuing with further scripting commands.
START /wait NET USE [driveletter:] \\ComputerName\ShareName
In our example we have:
Un altro esempio più specifico è :
START /wait NET USE X: \\client-0001\ernesto
The start /wait switch ensures that files can be read from the mapped drive immediately, in other words that subsequent commands in your script execute only after mapping is complete.
Syntax problem with NET USE
When using the NET USE command, you can run into some syntax-related errors. The System error 67 occurred is a very common one.
Also, if the ServerName that you provide contains spaces, you need to use quotation marks around the text. (that would be for example “Server Name”) Not providing quotation marks results in an error message: System error 85 has occurred.
Are there other related useful networking commands?
The NET SHARE command is used at the server to share a folder to others. If you want to access this shared resource from a client, you would use the NET SHARE command.
This page provides an overview of all available networking server commands: server NET commands.
NET USE syntax
The following is the syntax for NET USE:
net use
[{DEVICE | *}]
[\\COMPUTER\SHARE[\VOL]]
[{PASSWORD | *}]]
[/USER:[DOMAIN\]USER]
[/USER:[DOTTEDDOMAIN\]USER]
[/USER: [USER@DOTTEDDOMAIN]
[/SAVECRED]
[/SMARTCARD]
[{/DELETE | /PERSISTENT:{yes | no}}]
net use [DEVICE [/HOME[{PASSWORD | *}] [/DELETE:{yes | no}]]
net use [/PERSISTENT:{yes | no}]
That is about it.
OSFMount
OSFMount
OSFMount allows you to mount local disk image files (bit-for-bit copies of a disk partition) in Windows with a drive letter. You can then analyze the disk image file with PassMark OSForensics™ by using the mounted volume’s drive letter. By default, the image files are mounted as read only so that the original image files are not altered.
OSFMount also supports the creation of RAM disks, basically a disk mounted into RAM. This generally has a large speed benefit over using a hard disk. As such this is useful with applications requiring high speed disk access, such a database applications, games (such as game cache files) and browsers (cache files). A second benefit is security, as the disk contents are not stored on a physical hard disk (but rather in RAM) and on system shutdown the disk contents are not persistent.
OSFMount supports mounting images of CDs, which can be useful when a particular CD is used often and the speed of access is important.
Supported File Extensions
OSFMount supports the mounting of the following Windows image file formats:
| Image Format | Read | Write | Mount as RAM drive | Convert to Image file | Extend | Format |
| Raw Image (.IMG, .DD) | ||||||
| Raw CD Image (.ISO, .BIN) | ||||||
| Split Raw Image (.00n) | ||||||
| Nero Burning ROM Image (.NRG) | ||||||
| System Deployment Image (.SDI) | ||||||
| Advanced Forensics Format Images* (AFF) | ||||||
| Advanced Forensics Format Images w/ meta data* (AFM) | ||||||
| Advanced Forensics Format Directories* (AFD) | ||||||
| VMWare Image (.VMDK) |
* The supported version of Advanced Forensics Format is AFFv3 with zlib compression support. Encryption and signatures are not supported.
System Requirements
Windows XP, Vista & Win 7
Windows Server 2000, 2003, 2008
32bit and 64bit support
It is recommended that 64-bit Windows is used when large disk image files are to be mounted. The 32-bit version can only be used on 32-bit Windows. The 64-bit version can only be used on 64-bit Windows.
Users must have administrator privileges.
RAM: 1GB. When mounting large disk images, the more RAM the better.
Disk space: 1 MB of free hard disk space for the installation files.
Homepage: http://www.osforensics.com/tools/mount-disk-images.html
Download 32bit: http://www.osforensics.com/downloads/osfmount.exe
Download 64bit: http://www.osforensics.com/downloads/osfmount_x64.exe
Gpg4win
Gpg4win
Gpg4win (GNU Privacy Guard for Windows) is an encryption software for files and emails.
What is Gpg4win?
Gpg4win enables users to securely transport emails and files with the help of encryption and digital signatures. Encryption protects the contents against an unwanted party reading it. Digital signatures make sure that it was not modified and comes from a specific sender.
Gpg4win supports both relevant cryptography standards, OpenPGP and S/MIME (X.509). Gpg4win is the official GnuPG distribution for Windows and is maintained by the developers of GnuPG. Gpg4win and the software included with Gpg4win are Free Software (Open Source; among other things free of charge for all commercial and non-commercial purposes).
Creation of Gpg4win was supported by the German Federal Office for Information Security (BSI).
Gpg4win Components
Gpg4win is an installer for Windows and contains several Free Software components:
- GnuPG – The core; this is the actual encryption tool.
- Kleopatra – A certificate manager for OpenPGP and X.509 (S/MIME) and common crypto dialogs.
- GPA – An alternative certificate manager for OpenPGP and X.509 (S/MIME).
- GpgOL – A plugin for Microsoft Outlook 2003 and 2007 (email encryption).
- GpgEX – A plugin for Microsoft Explorer 32bit (file encryption).
- Claws Mail – A complete email application with crypto support.
- Gpg4win Compendium – The documentation (for beginner and advanced users), available in English and German.
System Requirements
Gpg4win runs on Windows 2000, XP, Vista and 7. Both 32 and 64bit systems are supported.
The Outlook plugin GpgOL is compatible with Microsoft Outlook 2003 and 2007. Outlook 2010 is not supported.
Important: Currently, the Windows Explorer plugin GgpEX works with 32bit Explorer only. It is possible to use the 32bit Explorer on some 64bit Windows. A 64bit update is in progress. All file crypto features of GpgEX on Windows 64bit can be accessed from the file menu of Kleopatra (e.g. File > Sign/encrypt file).
Homepage: http://www.gpg4win.org/index.html
Manual Page: http://www.gpg4win.org/documentation.html
Download page: http://www.gpg4win.org/download.html
Imager Resizer
Image Resizer
Image Resizer for Windows is a utility that lets you resize one or more selected image files directly from Windows Explorer by right-clicking. I created it so that modern Windows users could regain the joy they left behind with Microsoft’s Image Resizer Powertoy for Windows XP.
Homepage: http://imageresizer.codeplex.com/
Download page: http://imageresizer.codeplex.com/releases/view/30247
Run InPrivate Mode Automatically when you run Internet Explorer 9
Run InPrivate Mode Automatically when you run Internet Explorer 9
If you like running your IE9 in InPrivate Mode, you will notice the ability to run InPrivate Mode Automatically has been removed by Microsoft.
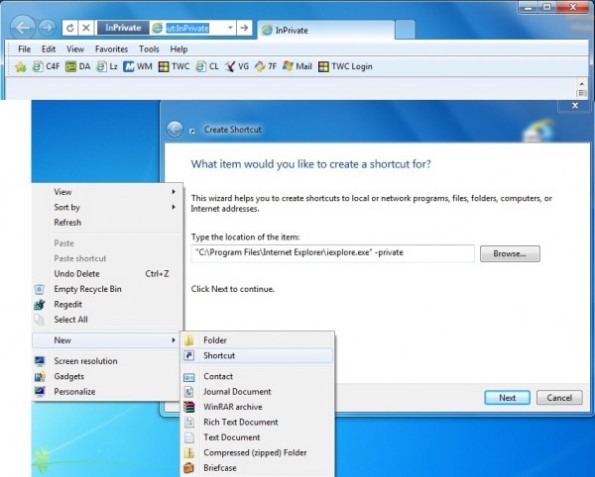
The alternative to running in InPrivate Mode Automatically is to create a shortcut to InPrivate Mode, For example a new IE shortcut on your desktop
- Right-Click on the desktop, Select New, next select Shortcut.
- Type the following in the path box: “C:\Program Files\Internet Explorer\iexplore.exe” -private (The path will be the path to Internet Explorer, then add -private after ending quotes)
Click next and give it a name. Now you can run InPrivate Mode Automatically by running the shortcut






Recent comments